A ransomware attack can be terrifying. Immediate action is crucial.
If you suspect a ransomware attack, you must quickly protect your data and minimize damage. Ransomware is malicious software that locks you out of your files until you pay a ransom. It’s a growing threat that affects individuals and businesses alike. Knowing what to do can make a huge difference. This guide will walk you through the essential steps to take if you suspect a ransomware attack. From isolating your device to seeking professional help, we’ll cover what you need to know to safeguard your information and potentially recover your files without paying the ransom. Stay calm, and follow these steps to take control of the situation. For added security, consider using NordVPN. Its advanced encryption and threat protection features can help you stay safe online. Secure your devices with NordVPN today.

Credit: www.lpl.com
Introduction To Ransomware Attacks
Ransomware attacks are rising. They can lock you out of your data. Hackers demand payment to restore access. Acting quickly is crucial to minimize damage.
Understanding Ransomware
Ransomware is a type of malware. It encrypts your files. You cannot access your data without a decryption key. Hackers use this to demand a ransom, usually in cryptocurrency.
There are two main types of ransomware:
Locker Ransomware: Locks you out of your device.
Crypto Ransomware: Encrypts your files.
Both types can cause significant disruption. Preventative measures and swift action are necessary.
Importance Of Immediate Action
If you suspect a ransomware attack, act quickly. Delays can lead to greater damage and data loss. Here are steps to take immediately:
Disconnect from the internet to prevent further spread.
Use antivirus software to scan and remove the malware.
Contact a cybersecurity expert for assistance.
In the digital age, staying protected is crucial. NordVPN can help. It encrypts your internet connection, hiding your IP address and location. This adds a layer of security, making it harder for hackers to target you.
Feature | Benefit |
|---|---|
Uninterrupted Streaming | No limits on bandwidth or speed |
Next-Generation Encryption | Keeps your online data safe |
Malware Protection | Blocks trackers and hides ads |
Strict No-Log Policy | Does not store private information |
Multi-Device Protection | Secure up to ten devices |
For more information, visit the NordVPN website.
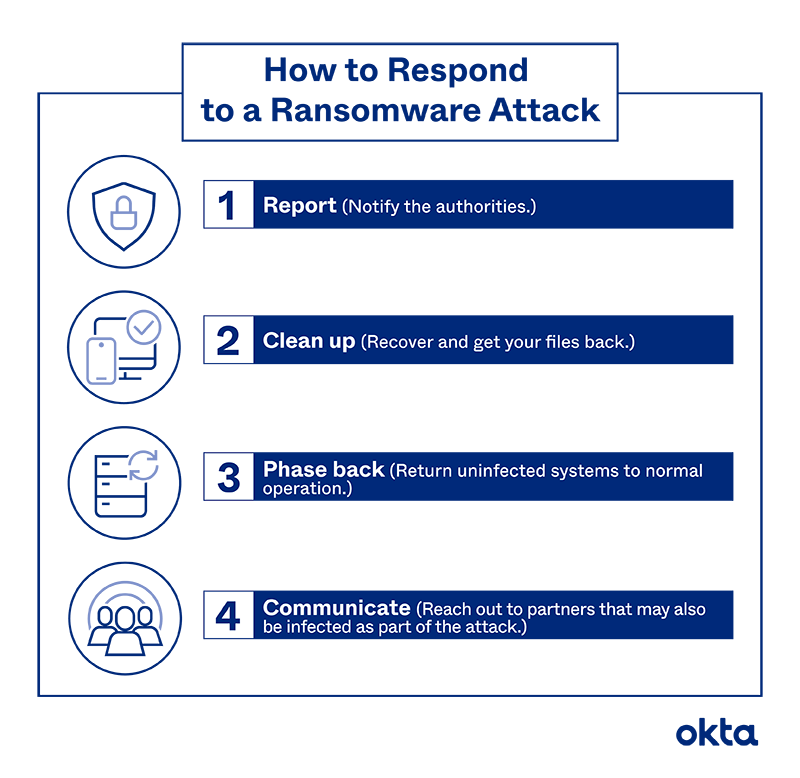
Credit: www.okta.com
Identifying A Ransomware Attack
Ransomware attacks are becoming more common and can be devastating. Identifying an attack early can help you respond quickly and minimize damage. Knowing the signs and types of ransomware is essential for effective detection.
Common Signs Of Ransomware
Unusual System Behavior: Your computer slows down without reason, or files become inaccessible.
Ransom Note: You receive a message demanding payment to regain access to your files.
Locked Screens: Your screen is locked with a message from the attacker.
File Extensions Change: File names change to unusual extensions, like .locked or .encrypted.
Increased Network Activity: Unusual data transfers or network usage spikes.
Disabled Security Software: Your antivirus or security software is suddenly disabled.
Types Of Ransomware
Type | Description |
|---|---|
Crypto Ransomware | Encrypts files and demands payment for the decryption key. |
Locker Ransomware | Locks your entire system, preventing access to any files or applications. |
Scareware | Presents fake warnings about system issues, demanding payment to fix them. |
Doxware | Threatens to release personal data unless a ransom is paid. |
RaaS (Ransomware as a Service) | Ransomware is sold as a service, making it accessible to non-technical attackers. |
Immediate Steps To Take If You Suspect A Ransomware Attack
If you suspect a ransomware attack, swift action is crucial. The following steps can help you mitigate the damage and secure your system. This guide will walk you through the necessary actions.
Disconnect From The Network
Firstly, disconnect your device from the network immediately. This step prevents the ransomware from spreading to other devices on the same network.
Unplug the Ethernet cable.
Turn off the Wi-Fi connection.
Disable Bluetooth and any other wireless connections.
By isolating the infected device, you reduce the risk of further contamination. This step is essential for containing the malware.
Assess The Scope Of The Attack
Next, assess the scope of the attack. Identify which files and systems are affected.
Check for ransom notes or messages on your screen.
Identify the type of ransomware by the file extension or ransom demand.
Scan your system using antivirus software to detect the malware.
Understanding the extent of the infection helps you plan your next steps. Document any findings for future reference.
Use a secondary device to research the specific ransomware type. This can provide insights into possible decryption tools or solutions.
Step | Action |
|---|---|
1 | Disconnect the affected device from the network. |
2 | Identify the type of ransomware involved. |
3 | Document findings and research potential solutions. |
Taking these immediate steps can significantly limit the damage caused by a ransomware attack. Act quickly and methodically to protect your data and systems.

Credit: solacecyber.co.uk
Reporting The Attack
Suspecting a ransomware attack can be alarming. Quick and effective reporting is crucial. This section outlines the essential steps for informing the right parties. Ensuring everyone is aware can help contain the threat and minimize damage.
Informing Internal Teams
First, alert your internal IT team. They need to assess and confirm the ransomware attack. Provide them with all available details, such as:
Time and date of the suspicious activity
Affected systems or files
Error messages or ransom notes
Next, notify senior management and key stakeholders. They must be aware of the potential risks and operational impacts. Ensure regular updates to keep everyone informed.
Contacting Law Enforcement
After informing internal teams, contact law enforcement. Reporting ransomware attacks to authorities can help track and mitigate the threat. Provide the following information:
Detailed description of the attack
Any communication with the attackers
Steps taken so far to contain the attack
Authorities may guide you on legal actions and further steps to take. They can also offer resources and support for dealing with ransomware incidents.
Containment And Mitigation
Suspecting a ransomware attack can be a nightmare. Immediate containment and mitigation are crucial to limit damage. This section will guide you through isolating infected systems and disabling remote access to mitigate the threat effectively.
Isolating Infected Systems
First, identify and isolate infected systems from the network to prevent the ransomware from spreading. Disconnect affected devices from the network immediately. This includes wired, wireless, and Bluetooth connections.
Consider the following steps:
Unplug the Ethernet cable.
Disable Wi-Fi connectivity.
Turn off Bluetooth.
Use a secure and clean device to communicate with your IT team. Ensure the infected systems remain powered on to preserve evidence for forensic analysis.
Disabling Remote Access
Disabling remote access is vital to prevent the attacker from gaining further control. Disable Remote Desktop Protocol (RDP) and other remote access services on the infected devices.
Follow these steps:
Access the control panel or system settings.
Navigate to the remote access settings.
Turn off RDP and other remote access features.
Ensure your firewall rules and VPN settings are updated to block unauthorized access. Consider using a service like NordVPN for enhanced security. NordVPN offers advanced encryption and malware protection to safeguard your systems.
By isolating infected systems and disabling remote access, you can significantly reduce the spread of ransomware and protect your network. Implement these steps swiftly to mitigate the impact of the attack.
Evaluating The Damage
If you suspect a ransomware attack, the first step is to evaluate the damage. This involves checking which files have been encrypted and understanding the extent of data loss. Doing so lets you determine the necessary steps to take next and plan your recovery process effectively.
Identifying Encrypted Files
Start by identifying encrypted files. Ransomware often changes file extensions, making it easy to spot affected files. Look for unusual file extensions or those that have been renamed.
Check shared folders like Documents, Downloads, and Desktop.
Use file recovery tools to identify encrypted files.
Some ransomware types add a specific extension to the files they encrypt. Knowing the extension can help you identify the type of ransomware you are dealing with.
Determining Data Loss
Next, focus on determining data loss. Assess which files have been compromised and whether you have recent backups. Compare current files with your backup copies to understand the extent of the loss.
Check the integrity of your backup data.
List down the critical data that is missing.
If you have a recent backup, you can restore your data. If not, you should seek professional help to recover the lost files.
Step | Description |
|---|---|
Identify Encrypted Files | Look for unusual file extensions and use file recovery tools. |
Determine Data Loss | Compare current files with backups to assess the extent of the loss. |
By carefully evaluating the damage, you can decide on the best course of action. Whether you need to restore from backups or seek professional help, understanding the extent of the damage is crucial.
Restoring From Backups
Suspecting a ransomware attack can be a nightmare. One of the most effective steps to take is restoring from backups. Doing so can help you regain control and reduce data loss. But how can you ensure a smooth and secure restoration process? Let’s explore some key aspects.
Using Clean Backups
Always use clean backups free from ransomware. This ensures you don’t reintroduce the malware into your system. Follow these steps:
Disconnect the infected device from the network.
Identify the most recent clean backup.
Scan the backup with reliable antivirus software.
Restore the data onto a clean device.
Using clean backups minimizes the risk of further infection. It allows you to restore your system to a safe state.
Verifying Backup Integrity
Before restoring, it’s crucial to verify the integrity of your backups. This ensures the data is complete and uncorrupted. Follow these guidelines:
Check the backup logs for errors or warnings.
Test the backup by restoring a small sample of data.
Confirm the restored data is accurate and functional.
Regularly verifying backup integrity ensures you have reliable data to restore in case of a ransomware attack. It’s an essential part of your data recovery strategy.
Step | Action |
|---|---|
1 | Disconnect the infected device |
2 | Identify a recent clean backup |
3 | Scan backup for malware |
4 | Restore data to a clean device |
5 | Check backup logs |
6 | Test restore sample data |
7 | Confirm data accuracy |
Following these steps can effectively restore your system from backups after a ransomware attack. Remember, regular backup maintenance is key to a smooth recovery process.
Prevention And Future Protection
If you suspect a ransomware attack, focusing on prevention and future protection is crucial. Implementing robust security measures and keeping software current can significantly reduce the risks.
Implementing Strong Security Measures
One of the most effective strategies is to implement strong security measures. Use advanced tools and services like NordVPN to enhance your online security.
Next-Generation Encryption: NordVPN uses AES-256 encryption to protect your data.
Threat Protection: Scans downloads for malware, blocks trackers, and hides ads.
Strict No-Log Policy: Does not collect or store any private information.
These features help create a secure environment, making it harder for ransomware to penetrate your systems.
Regularly Updating Software
Keeping your software up to date is another critical step. Regular updates patch vulnerabilities that ransomware can exploit.
Enable automatic updates for your operating system.
Regularly update all applications and software.
Use tools like NordVPN to ensure secure connections and protect against threats.
By following these steps, you can maintain a secure digital environment and reduce the risk of ransomware attacks.
Frequently Asked Questions
What Is The First Thing To Do In A Ransomware Attack?
Disconnect your device from the internet immediately to prevent the ransomware from spreading to other devices.
What Steps Should You Take If You Get Ransomware Attacked?
Disconnect from the internet immediately. Inform your IT team. Avoid paying the ransom. Report the attack to authorities. Restore data from backups.
What Is A Common Indicator Of A Ransomware Attack?
A standard indicator of a ransomware attack is the sudden inability to access files, accompanied by a ransom note demanding payment.
What Is The First Action After A Ransomware Attack?
Disconnect all infected devices from the network immediately. This helps prevent the ransomware from spreading further.
Conclusion
Act fast if you suspect a ransomware attack. Disconnect from the internet immediately. Notify your IT team or a cybersecurity expert. Please do not pay the ransom; it encourages more attacks. Backup your files regularly to avoid data loss. Consider using a reliable VPN for added security. NordVPN can help protect your online activities. Stay vigilant and keep your software updated. Prevention is the best defense against ransomware. Keep your systems secure and your data safe.
