In today’s digital age, protecting personal information online is more crucial than ever. Cyber threats are evolving, and our data is at constant risk.
Staying safe online requires a proactive approach. Simple steps can significantly enhance digital security, from secure passwords to VPNs. Personal information, when compromised, can lead to identity theft, financial loss, and other serious consequences. That’s why adopting best practices that safeguard your data is vital. This guide will explore practical strategies to protect your personal information online. By the end, you’ll have actionable tips to secure your data and maintain privacy in the digital world. For added security, consider using a trusted VPN like NordVPN to encrypt your internet connection and keep your online activities private. Learn more about NordVPN here.
Credit: lifelock.norton.com
Introduction To Protecting Personal Information Online
In today’s digital world, protecting personal information online is crucial. With increasing cyber threats, safeguarding your data has never been more critical. This section will introduce why protecting your personal information online and an overview of common online threats is essential.
Why Protecting Personal Information Is Important
Personal information includes your name, address, phone number, and financial details. If this information falls into the wrong hands, it can lead to identity theft, economic loss, and other serious issues.
Identity Theft: Cybercriminals can use your personal information to impersonate you.
Financial Loss: Unauthorized access to your financial data can result in stolen money.
Privacy Breach: Your private life may be exposed to the public.
Overview Of Common Online Threats
Understanding the common online threats is the first step in protecting your personal information. Here are some of the most prevalent dangers:
Threat | Description |
|---|---|
Phishing | Fraudulent attempts to obtain sensitive information by pretending to be a trustworthy entity. |
Malware | Malicious software designed to harm your device or steal data. |
Ransomware | Malware that locks you out of your files until you pay a ransom. |
Data Breaches | Unauthorized access to confidential data, often from large databases. |
Using a VPN like NordVPN can help protect your personal information. NordVPN offers advanced encryption, a no-logs policy, and multiple device support, ensuring your data remains private and secure.
Understanding Personal Information And Its Risks
In today’s digital age, protecting your personal information online is crucial. Understanding personal information and how it can be exploited helps safeguard your digital identity.
What Constitutes Personal Information
Personal information includes any data that can identify you. This encompasses:
Full Name
Address
Email Address
Phone Number
Social Security Number
Bank Account Details
Passwords
Even seemingly harmless information, like your pet’s name or birthdate, can be used by cybercriminals.
How Cybercriminals Exploit Personal Information
Cybercriminals use various methods to exploit personal information:
Phishing Attacks: Trick you into revealing sensitive information via fake emails or websites.
Malware: Infect devices to steal data and monitor activities.
Data Breaches: Hack into databases to obtain large volumes of information.
Social Engineering: Manipulate you into divulging personal details.
Once they have your information, they might:
Commit Identity Theft: Use your details to open accounts or make purchases in your name.
Financial Fraud: Access your bank accounts or credit cards for unauthorized transactions.
Blackmail: Threaten to release sensitive information unless you pay a ransom.
Understanding these risks highlights the importance of using a reliable VPN service like NordVPN to protect your online activities. NordVPN offers features like advanced encryption (AES-256), a no-logs policy, and tools such as Threat Protection to safeguard your personal information.
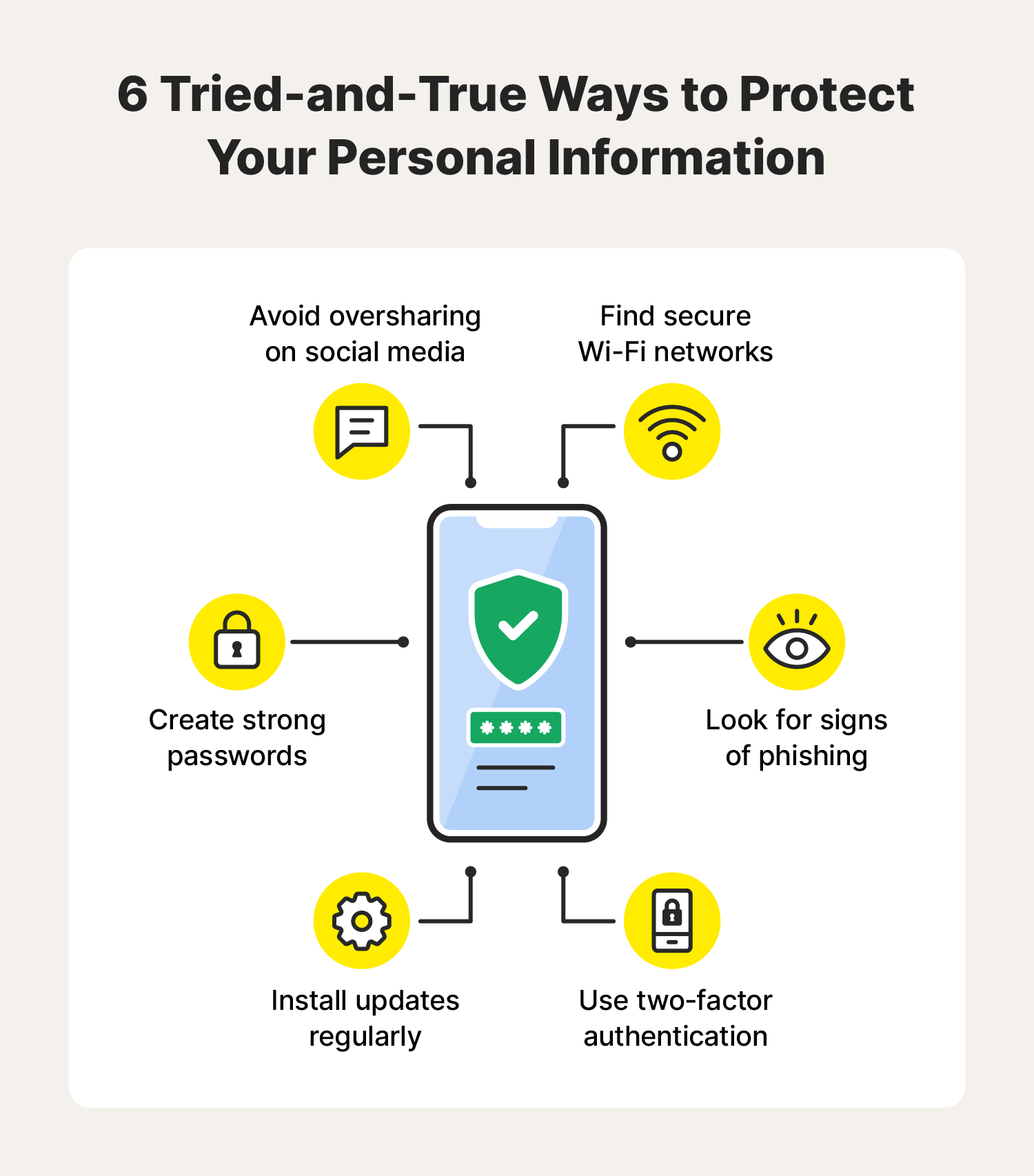
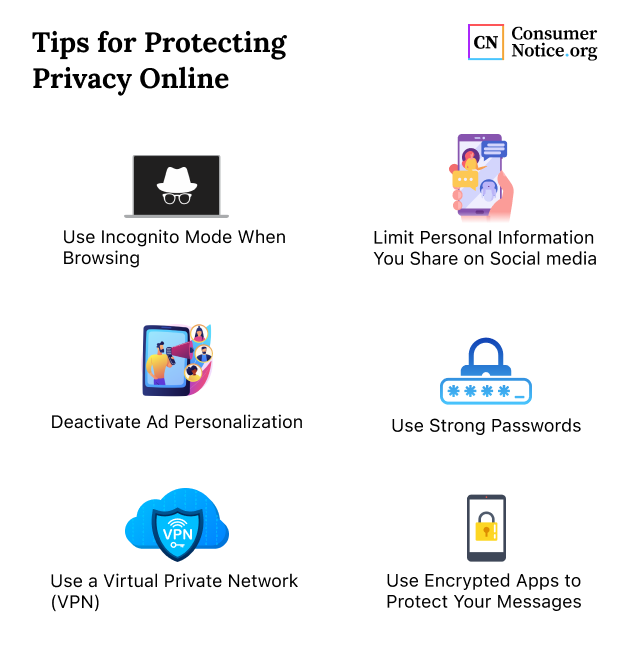
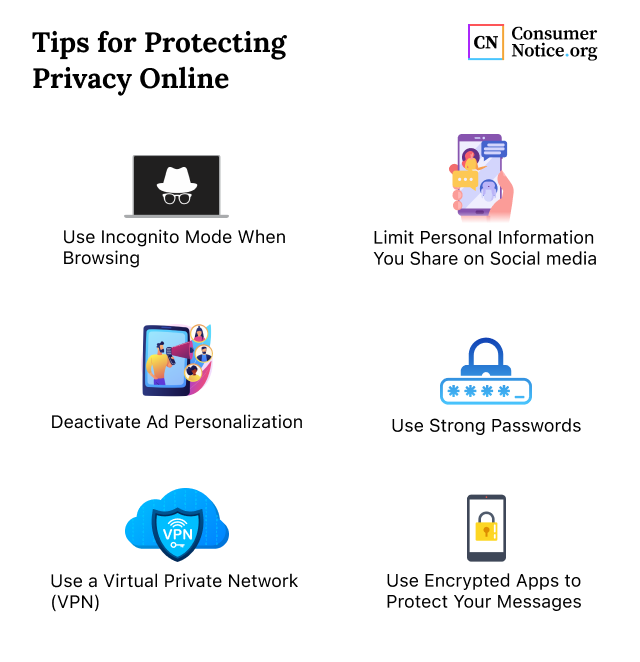
Key Best Practices For Online Privacy Protection
Protecting personal information online is crucial in today’s digital age. Implementing effective strategies can help safeguard your data from cyber threats. Here are some key best practices for maintaining online privacy.
Creating Strong And Unique Passwords
Using strong and unique passwords is vital for protecting your online accounts. Consider these tips:
Include a mix of letters, numbers, and special characters.
Avoid using common words or quickly guessable information.
Utilize a password manager to generate and store complex passwords securely.
Implementing Two-factor Authentication
Two-factor authentication (2FA) adds an extra layer of security. It requires not only a password but also a second form of verification:
Use apps like Google Authenticator or Authy for one-time codes.
Enable 2FA on all accounts that offer it, including email and social media.
Regularly Updating Software And Devices
Keeping your Software and devices up to date is essential for security. Regular updates patch vulnerabilities and enhance protection:
Set automatic updates for operating systems and applications.
Regularly check for firmware updates on devices such as routers.
Utilizing Secure wi-fi Networks
Using secure wi-fi networks is critical, especially when accessing sensitive information:
Avoid using public wi-fi for financial transactions or accessing private data.
Use a VPN like NordVPN to encrypt your connection and protect your information. NordVPN offers next-generation encryption and a strict no-log policy.
Ensure your home wi-fi is secured with a strong password and WPA3 encryption.
Following these best practices can significantly improve your online privacy and protect your personal information from cyber threats. For additional security, consider using NordVPN, which offers advanced encryption and a user-friendly interface to keep your data safe.
Credit: www.consumernotice.org
Securing Personal Devices And Accounts
Securing personal devices and accounts is essential for protecting your personal information online. Implementing best practices ensures your data remains safe from unauthorized access. Below are key strategies to help you secure your devices and online accounts effectively.
Best Practices For Device Security
Use Strong Passwords: Create complex passwords with letters, numbers, and symbols.
Enable Two-Factor Authentication: Add an extra layer of security by requiring a second form of verification.
Keep Software Updated: Regularly update your operating system and applications to protect against vulnerabilities.
Install Antivirus Software: Use reliable antivirus software to detect and remove Malware.
Encrypt Your Data: Use encryption tools to protect sensitive information on your devices.
Lock Your Devices: Set automatic locks and use strong passwords or biometric authentication.
Tips For Protecting Online Accounts
Use Unique Passwords: Avoid reusing passwords across multiple accounts.
Monitor Account Activity: Regularly check your account activity for any unauthorized access.
Be Wary of Phishing Scams: Do not click on suspicious links or provide personal information to unknown sources.
Use a Password Manager: Tools like NordPass help securely generate and store complex passwords.
Secure wi-fi Connections: Avoid using public wi-fi for sensitive transactions. Use a VPN like NordVPN for added security.
Importance Of Regular Backups
Regularly backing up your data is crucial to avoid data loss. Here are some best practices:
Use Cloud Storage: Services like Google Drive or Dropbox provide secure and accessible storage options.
Schedule Automatic Backups: Set up automatic backups to ensure your data is always up-to-date.
Keep Multiple Copies: Store backups in different locations, such as external drives and cloud services.
Test Your Backups: Regularly verify that your backups are complete and can be restored.
Implementing these strategies for securing personal devices and accounts helps protect your personal information from cyber threats. Stay proactive and informed to maintain your online security.
Safe Browsing And Communication Habits
Maintaining safe browsing and communication habits is essential to protect personal information online. This section focuses on practical tips and best practices to secure your online activities.
Recognizing Phishing Attempts
Phishing attempts are fraudulent messages designed to steal personal information. Recognize them by looking for:
Suspicious sender addresses: Check if the email address is legitimate.
Urgent language: Beware of messages that create a sense of urgency.
Spelling and grammar mistakes: Phishing emails often contain errors.
Links and attachments: Hover over links to see the URL before clicking.
Always verify the source before providing any personal information.
Safely Sharing Personal Information Online
When sharing personal information online, consider these practices:
Limit sharing: Share only necessary details.
Use secure websites: Look for “https” in the URL.
Enable privacy settings: Adjust settings on social media to control who sees your information.
Avoid public wi-fi: Use a VPN like NordVPN to protect your data on public networks.
Be cautious and think twice before sharing sensitive information.
Using Encrypted Communication Channels
Encryption is crucial for secure communication. Here are some tips:
Use encrypted messaging apps: Apps like Signal or WhatsApp provide end-to-end encryption.
Encrypt emails: Use services that offer encryption, such as ProtonMail.
Use a VPN: A VPN like NordVPN encrypts your internet connection, ensuring privacy and security.
These methods help protect your communications from unauthorized access.
Credit: www.consumernotice.org
Tools And Technologies For Enhanced Privacy
Protecting personal information online requires the use of practical tools and technologies. These solutions enhance your privacy, making accessing your data harder for malicious actors. Below are some of the best tools and technologies to safeguard online privacy.
Using Vpns For Secure Internet Access
Virtual Private Networks (VPNs) are essential for secure internet access. A VPN like NordVPN encrypts your connection, hiding your IP address and location. This ensures that your online activities remain private.
NordVPN features:
Uninterrupted Streaming: No limits on bandwidth or speed, ensuring a smooth streaming experience.
Easy VPN Set Up: Simple installation with a few clicks, including a Quick Connect button for optimal server selection.
Next-Generation Encryption: Uses AES-256 encryption to keep your data safe, even on public wi-fi.
Malware Protection: Includes Threat Protection to scan downloads, block trackers, and hide ads.
Strict No-Log Policy: Does not collect or store private information such as bandwidth usage, traffic logs, IP addresses, or browsing data.
Browser Extensions For Privacy Protection
Browser extensions can significantly enhance your privacy. These tools block ads, trackers, and malicious websites. Popular extensions include:
Adblock Plus: Blocks annoying ads, improving page load times.
Privacy Badger: Blocks invisible trackers, ensuring that your browsing remains private.
HTTPS Everywhere: Automatically redirects to secure HTTPS versions of websites.
Antivirus And Anti-malware Software
Antivirus and anti-malware Software protect your devices from harmful Software. These tools scan your system for threats and remove them. Notable options include:
Norton Antivirus: Comprehensive protection against viruses, Malware, and other online threats.
Malwarebytes: Specializes in removing Malware that other programs might miss.
Bitdefender: Offers multi-layer ransomware protection and advanced threat defense.
Using these tools and technologies, you can significantly enhance online privacy and protect your personal information from cyber threats.
Privacy Settings On Popular Platforms
Protecting your personal information online starts with optimizing privacy settings on popular platforms. Understanding and adjusting these settings can help secure your data and maintain privacy.
Optimizing Social Media Privacy Settings
Social media platforms offer privacy settings to control who can see your information. Here are some tips for optimizing these settings:
Facebook: Review your privacy settings using the “Privacy Checkup” tool. Limit who can see your posts and personal information.
Twitter: Set your account to private to control who follows you. Review settings for tweet visibility and data sharing.
Instagram: Make your account private to ensure only approved followers can see your posts. Disable location sharing.
LinkedIn: Adjust profile visibility and limit who can view your connections and activity.
Adjusting Privacy Settings On Mobile Apps
Mobile apps often request permissions that may compromise your privacy. Follow these steps to adjust your app privacy settings:
Review App Permissions: Regularly check and adjust app permissions in your device settings. Only grant necessary permissions.
Disable Background Data: Prevent apps from accessing your data in the background to enhance privacy and save data.
Use VPN Services: Consider using a VPN like NordVPN for secure internet connections and to hide your IP address.
Understanding Privacy Policies
Reading and understanding privacy policies can help you make informed decisions about your data. Here are some key points to look for:
Data Collection: Understand what data the service collects and how it is used.
Data Sharing: Check if the service shares your data with third parties.
Data Retention: Know how long your data is stored and the conditions for its deletion.
User Rights: Be aware of your data access, correction, and deletion rights.
By optimizing privacy settings, adjusting mobile app permissions, and understanding privacy policies, you can better protect your personal information online.
Responding To Data Breaches And Identity Theft
Experiencing a data breach or identity theft can be overwhelming. Knowing how to respond can make a significant difference in minimizing the damage. Here, we will explore the necessary steps to take if your personal information is compromised, resources available for identity theft victims, and strategies to prevent future breaches.
Steps To Take If Your Personal Information Is Compromised
If you discover that your personal information has been compromised, act quickly. Here’s a step-by-step guide:
Alert your bank and credit card companies: Inform them about the breach and check for unauthorized transactions.
Change your passwords: Update passwords for all your online accounts, especially those related to the compromised data.
Monitor your accounts: Monitor bank statements and credit reports for unusual activity.
Enable two-factor authentication: Add an extra layer of security to your accounts.
Report the breach: Notify relevant authorities, such as the Federal Trade Commission (FTC) or local law enforcement.
Resources For Identity Theft Victims
Several resources are available to help victims of identity theft:
IdentityTheft.gov: This FTC website provides a recovery plan and steps to report identity theft.
Credit Bureaus: Contact significant credit bureaus (Experian, Equifax, and TransUnion) to place a fraud alert or freeze on your credit.
Identity Theft Resource Center: Offers free assistance and guidance for identity theft victims.
Preventing Future Breaches
Prevention is crucial to protect your personal information online. Consider these practices:
Practice | Description |
|---|---|
Use a VPN | Secure your internet connection with a VPN like NordVPN. It encrypts your data and hides your IP address. |
Regularly update software | Keep your operating system, browsers, and apps up-to-date to protect against vulnerabilities. |
Strong, unique passwords | Use complex passwords for different accounts. Consider a password manager to keep track. |
Be cautious with personal information | Limit sharing personal details on social media and other platforms. |
Implementing these practices can significantly reduce the risk of future breaches and enhance your online security.
Conclusion: Staying Vigilant And Proactive
Staying vigilant and proactive in protecting personal information online is crucial. With the rise of cyber threats, adopting best practices to safeguard your digital life is essential. Continuous learning and adaptation are key to staying ahead of potential risks.
Continuous Learning And Adaptation
Cybersecurity is an ever-evolving field. New threats emerge every day, making it necessary to stay informed. Regularly update yourself on the latest security practices and tools. For instance, a reputable VPN service like NordVPN can significantly enhance your security.
Stay Updated: Follow cybersecurity news and updates to stay informed about new threats.
Use Advanced Tools: Leverage tools like NordVPN for secure browsing and data protection.
Regular Updates: Keep your Software and applications updated to protect against vulnerabilities.
Empowering Yourself With Knowledge
Knowledge is power, especially in the digital world. Understanding the importance of online privacy and the tools available can empower you to make informed decisions.
For example, NordVPN offers features like Advanced Encryption (AES-256), which keeps your data safe even on public wi-fi. It also has a Strict No-Log Policy, ensuring your activities remain private.
Feature | Benefit |
|---|---|
Advanced Encryption (AES-256) | Protects data from unauthorized access |
Strict No-Log Policy | Keeps your online activities private |
Threat Protection | Blocks ads, trackers, and malware |
Take advantage of the resources and tools available to you. Use services like NordVPN to enhance your online security and privacy.
Frequently Asked Questions
What Are Some Best Practices For Protecting Personal Information Online?
Use strong passwords and change them regularly. Enable two-factor authentication. Avoid sharing personal information on social media. Keep Software and devices updated. Use reliable antivirus programs.
What Are 5 Ways To Protect Your Security Online?
Use strong, unique passwords. Enable two-factor authentication. Update Software regularly. Avoid clicking on suspicious links. Use a VPN for secure browsing.
How Can I Protect My Personal Information Online?
Use strong passwords and enable two-factor authentication. Avoid sharing personal information publicly. Use secure websites (HTTPS) and keep your Software updated. Be cautious with emails and links to avoid phishing scams. Use a reliable antivirus program.
What Are The Best Practices For Internet Security?
Use strong passwords and update them regularly. Enable two-factor authentication. Keep Software updated. Avoid clicking on suspicious links. Use antivirus and firewall protection.
Conclusion
Staying safe online is essential in today’s digital world. Protect your personal information with strong passwords and regular updates. Avoid sharing sensitive data on unsecured sites. Consider using a reliable VPN service like NordVPN for added security. This VPN offers top-notch encryption and privacy features. Maintaining good habits and using trusted tools can significantly enhance your online security. Stay vigilant and protect your data.
