DDoS attacks can cripple your website, causing major downtime and loss of revenue. Protecting your site from these malicious attacks is crucial to maintaining its availability and performance.
DDoS, or Distributed Denial of Service, attacks overwhelm your website with traffic, making it inaccessible to real users. These attacks can come from multiple sources, making them difficult to stop. To defend your site, you need robust security measures. This guide will help you understand how to stop DDoS attacks on your website, ensuring it remains secure and operational. From understanding how these attacks work to implementing effective solutions, you’ll learn the essential steps to safeguard your online presence. Consider using security tools like NordVPN to enhance your website’s defenses for advanced protection.
Understanding DDoS Attacks
In the digital age, ensuring your website’s security is crucial. DDoS attacks can disrupt your online presence, leading to loss of revenue and trust. Let’s dive deeper into understanding these attacks.
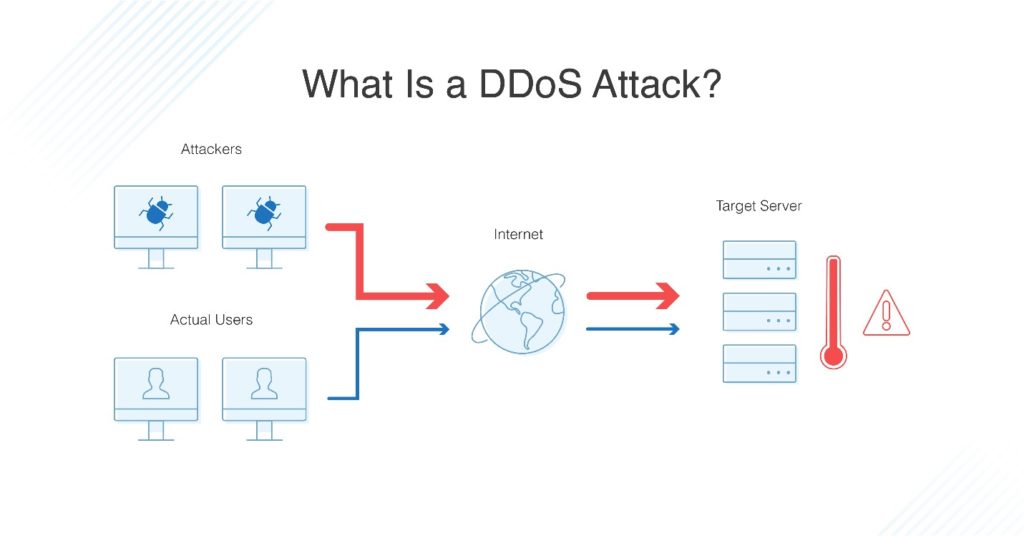
What Is A DDoS Attack?
A DDoS (Distributed Denial of Service) attack aims to overwhelm your website’s resources, making it inaccessible to users. Attackers use multiple devices to flood your server with traffic. The goal is to exhaust your server’s capacity, causing downtime.
How DDoS Attacks Work
Attackers exploit the limitations of your server’s capacity. They use various techniques to generate excessive traffic. This can include:
Sending numerous requests to your server
Utilizing botnets to amplify the attack
Exploiting server vulnerabilities
These attacks can last minutes, hours, or even days, severely impacting your website’s performance.
Common Types Of DDoS Attacks
Type | Description |
|---|---|
Volumetric Attacks | Massive amounts of data overwhelm the network’s bandwidth, causing congestion. |
Protocol Attacks | Exploits server resources by targeting network protocols like TCP/IP. |
Application Layer Attacks | Focuses on specific web applications, making it harder to detect. |
Understanding these types helps in creating effective countermeasures.

Credit: blog.sucuri.net
Signs Your Website Is Under A Ddos Attack
Recognizing the signs of a DDoS attack early can save your website from downtime and potential damage. Here are some common indicators that your site might be under attack:
Unusual Traffic Spikes
One of the first signs of a DDoS attack is a sudden and unexplained increase in traffic. This traffic surge usually comes from multiple sources, making it difficult to pinpoint the origin. If you notice a significant spike in traffic that is not aligned with your typical website patterns, it could be a DDoS attack.
Slow Or Unresponsive Website
A DDoS attack can overwhelm your server with requests, causing your website to become slow or unresponsive. Users might experience delays in page loading times or receive error messages indicating that the site cannot be reached. If your website performance drops dramatically without any apparent reason, consider the possibility of a DDoS attack.
Frequent Server Crashes
Repeated server crashes are another clear sign of a DDoS attack. The constant barrage of malicious traffic can cause your server to crash frequently, making your website unavailable to legitimate users. If you often reboot your server or notice unexplained downtime, your website might be under attack.
https://www.youtube.com/watch?v=p2oYg1byGJ8
Proven Strategies To Stop Ddos Attacks
Distributed Denial of Service (DDoS) attacks can cripple your website. Protecting your online presence requires strategic measures. Below, we discuss proven strategies to stop DDoS attacks.
Implementing Firewalls And Intrusion Detection Systems
Firewalls and Intrusion Detection Systems (IDS) are your first line of defense. They monitor and filter incoming traffic, identifying and blocking malicious data.
Firewalls: Create rules to block harmful traffic.
IDS: Detect and alert you of suspicious activities.
Use a combination of both to ensure comprehensive protection.
Using Content Delivery Networks (CDN)
Content Delivery Networks distribute your content across multiple servers globally. They help to absorb and distribute traffic during a DDoS attack.
Benefits of CDNs include:
Load Balancing: Spreads traffic to prevent overload.
Global Coverage: Reduces latency by serving content from the nearest server.
Examples of CDNs are Cloudflare and Akamai.
Rate Limiting And Traffic Filtering
Rate limiting controls the number of requests a user can make in a given time. It helps to mitigate the effects of DDoS attacks.
Steps to implement rate limiting:
Analyze normal traffic patterns.
Set thresholds to limit excessive requests.
Monitor and adjust limits as needed.
Traffic filtering blocks or flags unusual traffic patterns. Use these methods together for optimal results.
Deploying DDoS Protection Services
DDoS protection services offer specialized solutions to detect and mitigate attacks. They ensure your website remains operational during an attack.
Features of effective DDoS protection services:
Real-time Monitoring: Continuous traffic analysis to detect threats.
Automatic Mitigation: An immediate response is needed to block malicious traffic.
Scalability: Handle large-scale attacks with ease.
Examples include services from companies like Cloudflare and Akamai.
Advanced Techniques For Mitigating DDOS Attacks
Dealing with Distributed Denial of Service (DDoS) attacks requires advanced techniques. These methods ensure robust protection and maintain website availability. Here, we discuss some of the most effective strategies.
Behavioral Analytics For Anomaly Detection
Behavioral analytics is crucial in detecting anomalies. It monitors user behavior patterns and identifies irregular activities. This helps in spotting potential threats early.
Technique | Description |
|---|---|
Traffic Analysis | Monitors incoming traffic for unusual spikes or patterns. |
User Behavior Modeling | Establishes normal behavior baselines to detect deviations. |
Using these methods, you can mitigate threats before they escalate. This proactive approach is essential for maintaining website security.
Anycast Network Diffusion
Anycast network diffusion is another effective technique. It distributes traffic across multiple servers. This reduces the load on any single server, making it harder for attackers to overwhelm your system.
Load Balancing: Distributes network traffic to prevent overload.
Geographical Distribution: Servers are spread across different locations.
By diffusing traffic, you ensure better performance and resilience. This makes your website more robust against DDoS attacks.
Blackhole And Sinkhole Routing
Blackhole and sinkhole routing are effective in managing unwanted traffic. Blackhole routing drops malicious traffic before it reaches your network. Sinkhole routing, on the other hand, redirects it to a controlled environment.
Blackhole Routing: Drops all traffic to a null route.
Sinkhole Routing: Redirects traffic to a monitored environment.
These techniques help isolate and manage malicious traffic effectively. They ensure legitimate traffic is not affected, maintaining website availability.
Using these advanced techniques, you can significantly reduce the impact of DDoS attacks. Implementing these strategies ensures your website remains secure and accessible.
Proactive Measures To Prevent Future DDOS Attacks
Proactively preventing DDoS attacks is essential for maintaining your website’s security. Taking steps to fortify your defenses can save you from potential downtime and financial losses. Here are some key measures to consider:
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities in your website’s infrastructure. This involves a thorough examination of your network, applications, and hardware. By performing these audits frequently, you can detect and address weak spots before attackers exploit them.
Audit Type | Frequency | Key Focus Areas |
|---|---|---|
Network Audit | Quarterly | Firewalls, Routers, Switches |
Application Audit | Bi-Annually | Web Applications, APIs |
Hardware Audit | Annually | Servers, Storage Devices |
Updating And Patching Systems
Keeping your systems updated and patched is crucial for security. Software vendors regularly release updates to fix known vulnerabilities. Ensure that you apply these updates promptly to prevent exploitation by attackers.
Set up automatic updates for your operating systems, applications, and security software. This minimizes the risk of missing critical patches. Monitor updates and patches from your vendors to stay informed.
Creating A Ddos Response Plan
Having a DDoS response plan in place prepares your team for potential attacks. This plan should outline the steps during an attack to minimize damage and restore services quickly.
Identify Critical Assets: Determine which assets are most crucial to your operations.
Assign Roles and Responsibilities: Define who will handle specific tasks during an attack.
Develop Communication Protocols: Establish how to communicate with stakeholders and customers.
Test and Update Regularly: Conduct drills to ensure the plan is effective and current.
For enhanced protection, consider using a reliable VPN service like NordVPN. NordVPN offers advanced encryption, threat protection, and a strict no-logs policy. It can help secure your online activities and protect against various cyber threats. Learn more about NordVPN.
Credit: www.dnsstuff.com
Case Studies: Real-world Examples Of DDOS Mitigation
Understanding how real-world companies manage DDoS attacks can provide valuable insights. Let’s look at two case studies demonstrating effective DDoS mitigation strategies.
Successful DDOS Mitigation By A Large E-commerce Platform
A large e-commerce platform faced a significant DDoS attack that threatened its operations. The attack aimed to overwhelm its servers, causing downtime and potential revenue loss. The company implemented several mitigation techniques:
Web Application Firewall (WAF): Used a WAF to filter and monitor HTTP requests.
Rate Limiting: Applied rate limiting to control the traffic volume.
Content Delivery Network (CDN): Leveraged a CDN to distribute traffic loads across multiple servers.
These measures helped the platform maintain operational stability and protect its user data. The company’s proactive approach ensured minimal disruption and maintained customer trust.
How A Small Business Survived A Massive Ddos Attack
A small business with limited resources experienced a massive DDoS attack. The attack aimed to crash its website, causing significant downtime. The business adopted various strategies to mitigate the attack:
Cloud-Based DDoS Protection: Utilized a cloud-based DDoS protection service to absorb and deflect the attack.
Traffic Analysis: Conducted real-time traffic analysis to identify and block malicious IPs.
Scalable Infrastructure: Implemented a scalable infrastructure to handle traffic surges.
These strategies allowed the small business to withstand the attack and continue its operations. Despite the scale of the attack, the business’s resilience highlighted the importance of being prepared with robust security measures.

Credit: www.esecurityplanet.com
Frequently Asked Questions
Can DDoS Attacks Be Stopped?
Yes, DDoS attacks can be stopped. Implement firewalls, use DDoS protection services, and regularly update security measures.
What Is The Best Solution For A Ddos Attack?
The best solution for a DDoS attack is to use a cloud-based DDoS protection service. It provides robust, scalable security and mitigates attacks effectively.
Do I Need DDOS Protection For My Website?
Yes, you need DDoS protection. It safeguards your website from malicious attacks, ensuring uptime and security.
Does A Vpn Stop DDoS Attacks?
A VPN can help stop DDoS attacks by masking your IP address. This makes it harder for attackers to target your network.
Conclusion
Protecting your website from DDoS attacks is crucial. Implement the tips discussed to secure your site. Regular monitoring and proactive measures are key. For added security, consider using a reliable VPN service like NordVPN. It offers advanced encryption and privacy features. Stay safe, keep your data secure, and ensure uninterrupted online activities.
