An IP stresser or booter is a tool used to test network or server robustness by simulating a distributed denial-of-service (DDoS) attack. These tools can flood a target with traffic, potentially causing disruptions.
Understanding how these tools work is crucial for network security professionals and individuals interested in cybersecurity. IP stressors can serve legitimate purposes, such as testing a website to ensure it can handle high traffic. However, they can also be misused for illegal activities, such as launching attacks on websites or networks without permission. This dual nature makes it essential to know how these tools operate and the legal ramifications of their use. This post will explore the functionality and implications of IP stressors and booters, providing a comprehensive understanding of these powerful tools. For enhanced online security, consider using a reliable VPN service like NordVPN.
Introduction To IP Stressers And Booters
IP stressers and booters are tools often used in the realm of cybersecurity. These tools have specific purposes and functionalities that interest tech enthusiasts and security professionals.
Definition Of IP Stresser And Booter
An IP stressor is a tool designed to test the robustness of a network. It generates a lot of traffic to see if the network can handle it. This helps identify potential weaknesses in network infrastructure.
A booter is similar, but is often used maliciously. It sends excessive traffic to a target, overwhelming it and causing it to crash. This is also known as a DDoS (Distributed Denial of Service) attack.
Purpose And Common Uses
The primary purpose of an IP stresser is to test network stability. Network administrators use it to ensure their systems can handle high traffic volumes. This is crucial for maintaining robust and secure networks.
Testing network strength: Helps identify potential vulnerabilities.
Security analysis: Ensures a network can withstand high traffic without failing.
On the other hand, booters are often used for illicit purposes. They disrupt services by overwhelming networks with traffic.
Tool | Purpose |
|---|---|
IP Stresser | Testing network robustness |
Booter | Launching DDoS attacks |
Understanding these tools is vital for network security. Knowing their purposes helps prevent and mitigate potential threats.
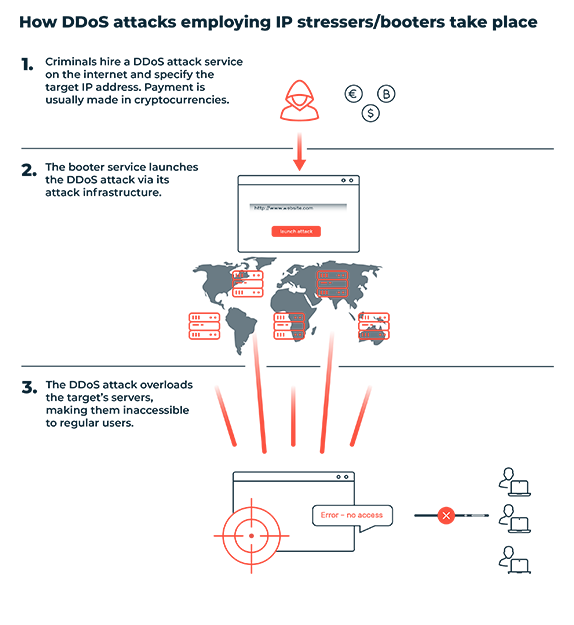
How IP Stressers And Booters Work
Understanding how IP Stressers and Booters work is crucial for grasping their impact on network security. These tools primarily perform Distributed Denial of Service (DDoS) attacks. Below, we break down their technical workings and the methods they employ.
Technical Overview
IP Stressers and Booters operate by overwhelming a target’s server or network with excessive traffic. This leads to network congestion, causing the service to slow down or become completely inaccessible.
These tools typically use a control panel where users can enter the target IP address and choose the type of attack. The software then sends packets to the target, exhausting its resources.
Common Techniques Used
UDP Flood: Sends many User Datagram Protocol packets to random ports on the target, overwhelming it.
HTTP Flood: Sends HTTP requests to a web server, consuming resources and bandwidth.
SYN Flood: Exploits the TCP handshake process, sending multiple SYN requests but never completing the handshake.
Role Of Botnets
Botnets play a significant role in amplifying the power of IP Stressers and Booters. A botnet is a network of compromised devices controlled by a single entity. These devices, often called ‘bots,’ are used to launch coordinated attacks.
By leveraging botnets, attackers can distribute the attack load across multiple machines, making the attack more potent and harder to mitigate.
Botnets are typically created by infecting devices with malware, which connects them to a central control server.
https://www.youtube.com/watch?v=2ZotIKMMCic
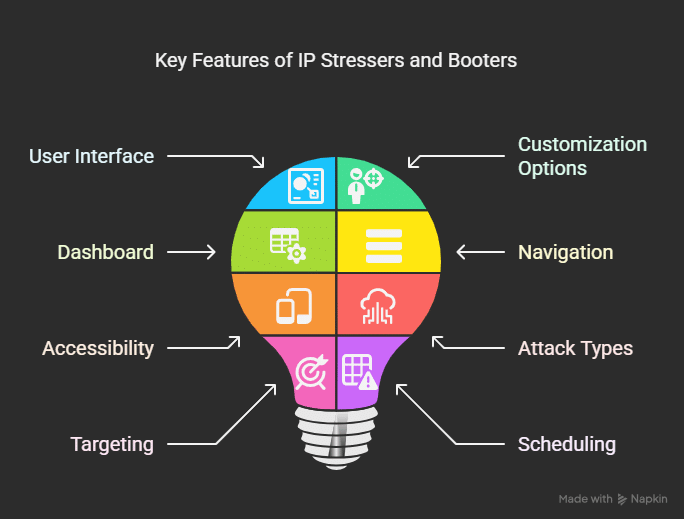
Key Features Of IP Stressers And Booters
IP Stressers and Booters are tools designed to test the robustness of a network. They simulate a Distributed Denial of Service (DDoS) attack, overwhelming the target with traffic. Understanding these tools’ key features helps evaluate their effectiveness and usability.
User Interface And Ease Of Use
The user interface of an IP Stresser or Booter should be intuitive. A clean and simple design ensures even those with minimal technical skills can navigate and use the tool. Most come with a dashboard that displays key metrics and options.
Dashboard: Centralized control panel for easy access to features.
Navigation: Simple menus and buttons for quick setup.
Accessibility: Compatible with various devices and screen sizes.
Customization Options
Customization is crucial in IP Stressers and Booters. It allows users to tailor the attack to fit specific needs. This includes setting the target IP, choosing the type of attack, and adjusting other parameters.
Attack Types: Options for different types of DDoS attacks.
Targeting: Ability to specify the target IP address or domain.
Scheduling: Plan attacks to occur at specific times.
Attack Strength And Duration
The strength and duration of the attack are critical features. These determine the impact of the stress test on the network. Users can adjust these settings to simulate various levels of network load.
Feature | Description |
|---|---|
Attack Intensity | Control the volume of traffic sent to the target. |
Duration | Set the length of time the attack will last. |
Frequency | Determine how often the attacks are repeated. |
These features ensure that IP Stressers and Booters provide a comprehensive way to test network resilience. Users can simulate various real-world scenarios by allowing adjustments in attack type, strength, and duration.
Credit: www.myrasecurity.com
Legality And Ethical Considerations
Understanding the legality and ethical considerations of using an IP stresser or booter. These tools can be used for legitimate purposes, but their misuse can have serious consequences. Let’s delve into the legal implications, ethical concerns, and potential impacts of misuse.
Legal Implications
IP stressors and booters can be legal if used for legitimate purposes, such as testing the robustness of your network. However, using these tools to disrupt or damage other networks is illegal in many jurisdictions. Laws such as the Computer Fraud and Abuse Act in the United States strictly prohibit unauthorized access and attacks on computer systems. Violating these laws can result in heavy fines and imprisonment.
Ethical Concerns
Using an IP stresser or booter ethically ensures proper authorization before testing any network. Unauthorized testing can harm network stability and disrupt users’ services. Always consider the potential impact on others and use these tools responsibly.
Consequences Of Misuse
Misusing IP stressors or booters can lead to severe consequences:
Legal Penalties: Including fines and imprisonment.
Network Damage: Causing disruptions that affect businesses and individuals.
Reputation Damage: Loss of trust and credibility in professional settings.
It’s crucial to understand the potential repercussions before using these tools. Always prioritize legality and ethical behavior.
Pricing And Affordability Of IP Stressers
IP Stressers or Booters are tools used to test the resilience of networks by simulating high traffic. Understanding the pricing and affordability of these tools is crucial for users. Let’s explore the typical pricing models and the cost vs. effectiveness of IP stressors.
Typical Pricing Models
The cost of an IP Stresser varies based on the features and the duration of usage. Here are some common pricing models:
Pay-as-You-Go: Users pay for the amount of traffic or time used. This model is flexible and cost-effective for occasional use.
Subscription-Based: Monthly or yearly plans offer unlimited usage within the subscription period. This model is suitable for frequent users.
Tiered Pricing: Different tiers provide various service levels, such as basic, standard, and premium. Higher tiers offer more features and better performance.
Cost Vs. Effectiveness
When evaluating the cost of IP Stressers, consider their effectiveness. A higher price often means better features and performance. Here’s a simple comparison:
Pricing Model | Cost (Approx.) | Effectiveness |
|---|---|---|
Pay-as-You-Go | USD 5-10 per hour | Effective for short-term testing |
Subscription-Based | USD 20-50 per month | Good for continuous testing |
Tiered Pricing | USD 10-100 per month | Highly effective with advanced features |
Ultimately, the choice depends on your specific needs and budget. Remember, investing in a reliable IP Stresser ensures comprehensive network testing.
Pros And Cons Of Using IP Stressors and Booters
IP stressers and booters are tools used to perform DDoS (Distributed Denial of Service) attacks. These tools can overload a server with excessive traffic, causing it to crash or become unavailable. While they have some legitimate uses, there are significant risks and drawbacks. Let’s explore the pros and cons of using IP stressers and booters.
Advantages For Users
IP stressors and booters offer some benefits for specific user groups. Here are some key advantages:
Network Testing: Network administrators use these tools to test the robustness of their systems. They can identify potential vulnerabilities and improve network defenses.
Performance Evaluation: IT professionals can evaluate the performance of their servers under heavy traffic. This helps optimize server resources and ensure better service delivery.
Cost-Effective: IP stressers and booters are relatively affordable compared to other network testing solutions. They provide an economical way to stress-test a network.
Potential Drawbacks And Risks
Despite their advantages, using IP stressors and booters comes with significant risks and drawbacks:
Illegal Use: Many users employ these tools for malicious activities. Conducting DDoS attacks against unauthorized targets is unlawful and punishable by law.
Collateral Damage: DDoS attacks can unintentionally affect other users. This can lead to service disruptions and financial losses for innocent parties.
Service Downtime: Using these tools irresponsibly can cause prolonged server downtime. This can harm a business’s reputation and result in lost revenue.
Security Risks: Users of IP stressers and booters may expose themselves to legal consequences. Additionally, these tools can be a gateway for hackers to exploit vulnerabilities in your network.
While IP stressors and booters can be useful for legitimate network testing, their potential for abuse and associated risks make them controversial in cybersecurity.
Recommendations For Responsible Use
Understanding IP stressors or booters is crucial, but responsible use is paramount. These tools can test network robustness, but misuse can lead to legal consequences. Below are recommendations to ensure responsible and ethical usage.
Ideal Users And Scenarios
Network Administrators: Use to test the resilience of their networks.
Security Professionals: Evaluate the security measures of a company’s infrastructure.
Educational Purposes: Teach students about network security and vulnerabilities.
IP stressers or booters should only be used by those with proper authorization. Unauthorized use can lead to severe penalties.
Best Practices For Safe Usage
Get Permission: Always obtain explicit permission before testing any network.
Use Ethical Tools: Opt for tools designed for legitimate testing.
Monitor Impact: Constantly monitor the impact on the network to avoid disruptions.
Document Everything: Keep records of all tests conducted, including the scope and results.
Stay Updated: Keep abreast of legal regulations surrounding the use of IP stressors.
Following these best practices ensures that your use of IP stressors remains within legal and ethical boundaries. Misuse can lead to serious repercussions, so always act responsibly.
Credit: www.myrasecurity.com
Frequently Asked Questions
How Do Booters Work?
Booters, or stressors, perform DDoS attacks to overwhelm and turn off targeted websites or networks. They use botnets to generate massive traffic.
Is IP Stressing Illegal In The US?
Yes, IP stressing is illegal in the US. It violates the Computer Fraud and Abuse Act (CFAA).
What Is DDoS? How Does It Work?
A DDoS attack is a cyberattack where multiple systems overwhelm a target, causing service disruption. Attackers flood the target with excessive traffic, making it inaccessible.
What Is An IP Stresser Used For?
An IP stressor is a tool used to test the robustness of servers. It sends traffic to the target server to check its capacity.
Conclusion
Understanding an IP stresser or booter is crucial for online security. These tools can overload servers, causing disruptions. Protect your network from such attacks. Use reliable security solutions. Consider using a VPN for added protection and privacy. NordVPN offers advanced encryption and a no-logs policy. It ensures safe and private browsing. Click here to learn more about NordVPN. Stay safe online and protect your data.
